Something that as bothered me for a long time is the ease with which bad actors can gain access to important infrastructure such as banks. It can be as simple as a click on a link by an employee that takes them to a potentially innocuous application: but he bad actor has gained access and can sit there doing nothing for months or years. The key is that they have access and can use that for malicious attacks later.
Security strategy today at banks tends to follow applications or products and leave the bank open to many attacks vectors.
Zero Trust
Zero Trust is a different approach predicated on the belief that bad actors are already in your network. The traditional approach of a castle and moat is guaranteed to fail and we see that in the news daily.
Zero trust and persistent security consider a paradigm shift in Cyber Security.
I recommend this podcast:
- (guests – Mr. David McKeown serves as the acting DoD principal deputy chief information officer and Dr. Richard J. Harknett is professor and director of the School of Public and International Affairs and chair of the Center for Cyber Strategy and Policy at the University of Cincinnati.)
Podcast details:
Seizing the Digital Initiative: Zero Trust and Persistence in the Cyber Domain – podcast: https://irregular-warfare-podcast.castos.com/episodes/seizing-the-digital-initiative-zero-trust-and-persistence-in-the-cyber-domain
Finally here is a well documented example of Zero Trust in practise.
The US Department of Defense – Zero Trust Strategy
Here is their description:
https://dodcio.defense.gov/Library/
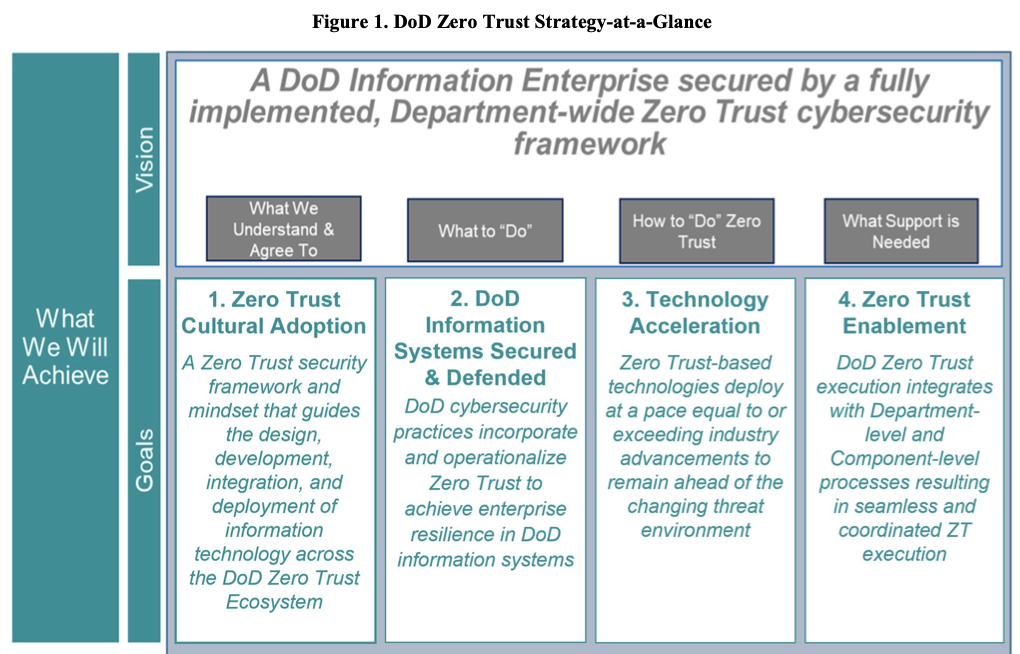
The strategy outlines four high-level and integrated strategic goals that define what the Department will do to achieve its vision for ZT:
• Zero Trust Cultural Adoption – All DoD personnel are aware, understand, are trained, and committed to a Zero Trust mindset and culture and support integration of ZT.
• DoD information Systems Secured and Defended – Cybersecurity practices incorporate and operationalize Zero Trust in new and legacy systems.
• Technology Acceleration – Technologies deploy at a pace equal to or exceeding industry advancements.
• Zero Trust Enablement – Department- and Component-level processes, policies, and funding are synchronized with Zero Trust principles and approaches.
Relevance to Bankwatch
A detailed analysis is beyond my scope however I am continuing to study how the risks DoD addresses are similar to that we see in our Banks. It would be a mistake to ignore because military is not a bank or vice versa.
As mentioned earlier, s simple castle and moat protection is too broad-based and flimsy. To paraphrase a recent President there is no wall strong, high enough, deep enough to offer adequate protection to that one bad actor access through spearfishing. And once the bad actor gains access the world is his oyster – just ask the most recent public attack at Indigo books in Canada.
But for every public attack there are 100’s of private attacks that are impacting consumers data. I have witness examples and it is not pretty.
Further reading:


